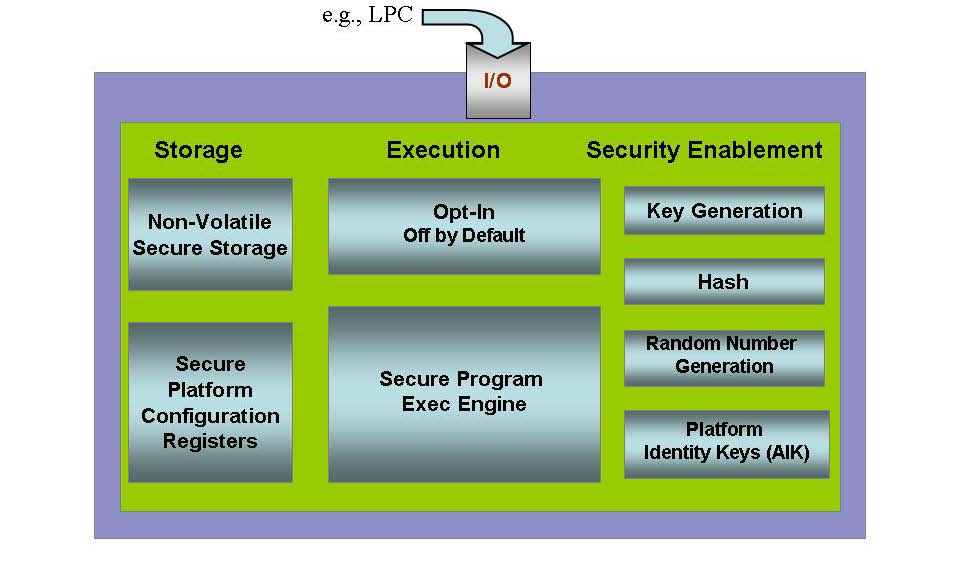
TPM or Trusted Platform Module as referred by TCG (Trusted Computing Group) is a microcontroller used in Laptop and now also on servers to ensure the integrity of the platform. TPM can securely store artifacts used to authenticate the platform. These artifacts can include passwords, certificates, or encryption keys. A TPM can also be used to store platform measurements that help ensure that the platform remains trustworthy. Authentication (ensuring that the platform can prove that it is what it claims to be) and attestation (a process helping to prove that a platform is trustworthy and has not been breached) are necessary steps to ensure safer computing in all environments.
 |
| source: http://www.trustedcomputinggroup.org |
Above image depicts the overall function of TPM module. Standard use case I have seen is ensuring secure boot process of servers. Secure boot will validate the code run at each step in the process, and stop the boot if the code is incorrect. The first step is to measure each piece of code before it is run. In this context, a measurement is effectively a SHA-1 hash of the code, taken before it is executed. The hash is stored in a platform configuration register (PCR) in the TPM.
Each TPM has at least 24 PCRs. The TCG Generic Server Specification, v1.0, March 2005, defines the PCR assignments for boot-time integrity measurements. The table below shows a typical PCR configuration. The context indicates if the values are determined based on the node hardware (firmware) or the software provisioned onto the node. Some values are influenced by firmware versions, disk sizes, and other low-level information.
Therefore, it is important to have good practices in place around configuration management to ensure that each system deployed is configured exactly as desired.
So there are very good use case of TPM to ensure secure boot and integrity of hardware - who all are using TPM? There are many institutions who runs their private clouds have been seen using TPM chipset on their servers while many public clouds do not support TPM - why? that's mystery!
TPM 1.2 only support SHA-1 algorithm
Each TPM has at least 24 PCRs. The TCG Generic Server Specification, v1.0, March 2005, defines the PCR assignments for boot-time integrity measurements. The table below shows a typical PCR configuration. The context indicates if the values are determined based on the node hardware (firmware) or the software provisioned onto the node. Some values are influenced by firmware versions, disk sizes, and other low-level information.
Therefore, it is important to have good practices in place around configuration management to ensure that each system deployed is configured exactly as desired.
| Register | What is measured | Context |
|---|---|---|
| PCR-00 | Core Root of Trust Measurement (CRTM), BIOS code, Host platform extensions | Hardware |
| PCR-01 | Host platform configuration | Hardware |
| PCR-02 | Option ROM code | Hardware |
| PCR-03 | Option ROM configuration and data | Hardware |
| PCR-04 | Initial Program Loader (IPL) code. For example, master boot record. | Software |
| PCR-05 | IPL code configuration and data | Software |
| PCR-06 | State transition and wake events | Software |
| PCR-07 | Host platform manufacturer control | Software |
| PCR-08 | Platform specific, often kernel, kernel extensions, and drivers | Software |
| PCR-09 | Platform specific, often Initramfs | Software |
| PCR-10 to PCR-23 | Platform specific | Software |
So there are very good use case of TPM to ensure secure boot and integrity of hardware - who all are using TPM? There are many institutions who runs their private clouds have been seen using TPM chipset on their servers while many public clouds do not support TPM - why? that's mystery!